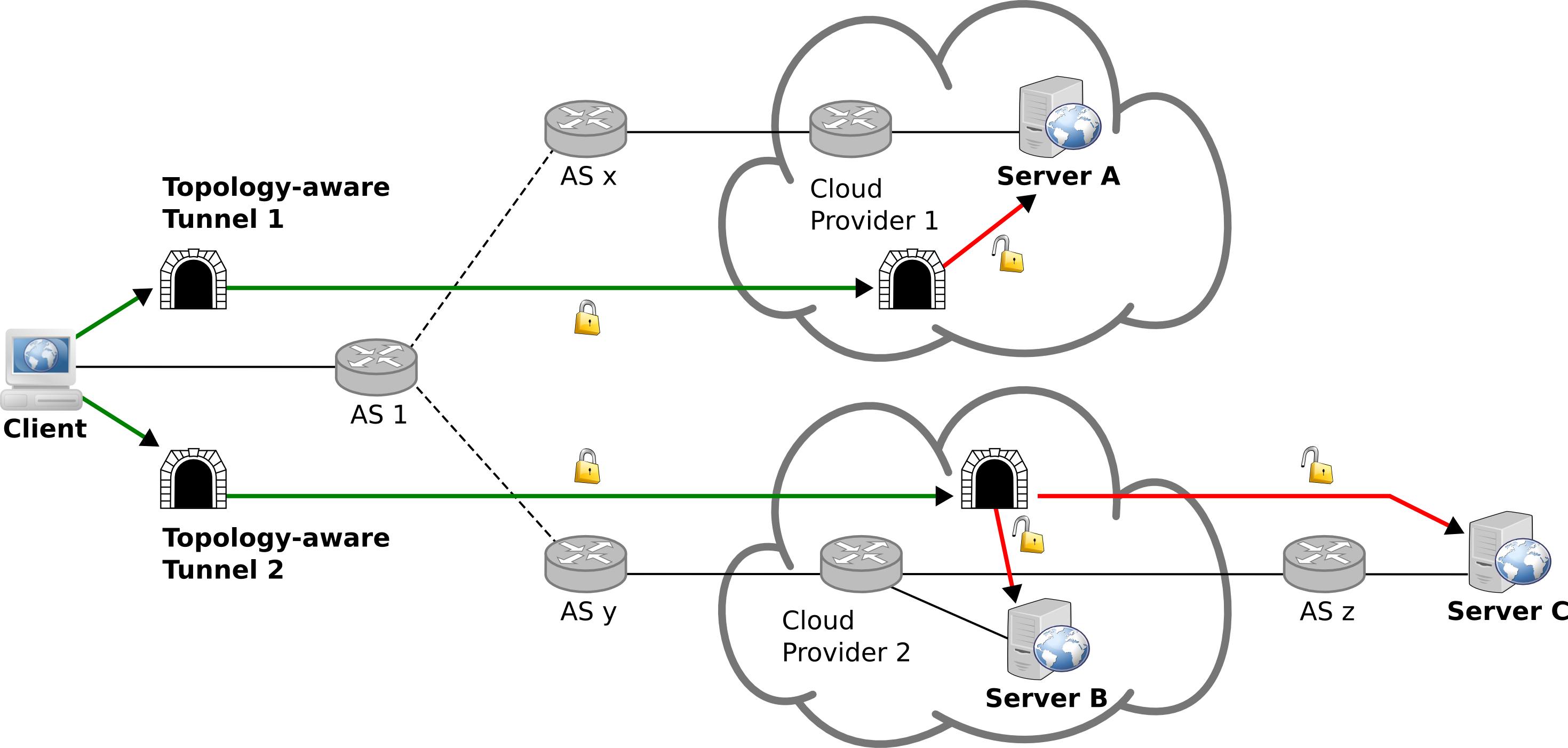
Unencrypted and unauthenticated protocols present security and privacy risks to end-to-end communications. Even when services support TLS, implementation vulnerabilities threaten their security. This research project proposes an architecture called Topology-aware Network Tunnels (TNT) which minimizes insecure network paths to Internet services without their participation. We argue that if end-to-end security with a server is not available the next best thing is a secure link to a network that is close to the server and will act as a gateway. We observe that popular web destinations are clustered inside cloud networks. This enables any user to strategically establish secure tunnels to these networks and route their traffic through them. As a result adversaries not able to compromise the web service or its hosting provider are presented with encrypted and authenticated traffic instead of today's plain text. The strategic placement of network tunnels, gathering of network intelligence and routing decisions of the TNT architecture are not found in VPN services, network proxies or Tor.
People
Georgios Kontaxis (E-Mail: kont...@cs.columbia.edu)
Angelos D. Keromytis (E-Mail: ange...@cs.columbia.edu)
Peer-reviewed Publications - Conference Papers
Protecting Insecure Communications with Topology-aware Network Tunnels. Georgios Kontaxis, and Angelos D. Keromytis. In Proceedings of the 23rd ACM Conference on Computer and Communications Security (CCS). October 2016, Vienna, Austria. (Acceptance rate: 16.5%) [Slides]